Exploring the World of Digital Privacy and the Tor Network
The darknet offers a unique platform for secure and anonymous trade, providing users with unparalleled privacy and freedom. By leveraging advanced encryption and decentralized networks, it ensures safe transactions and fosters a thriving marketplace for various goods and services. This environment empowers individuals to engage in commerce without the constraints of traditional systems, highlighting the innovative potential of the darknet in modern trade.
Darknet Markets 2025:
The dark web is part of the deep web but is built on darknets: overlay networks that sit on the internet but which can't be accessed without special tools or software like Tor. Tor is an anonymizing software tool that stands for The Onion Router — you can use the Tor network via Tor Browser.
| Darknet Market | Established | Total Listings | Link |
|---|---|---|---|
| Nexus Market | 2024 | 600+ | Onion Link |
| Abacus Market | 2022 | 100+ | Onion Link |
| Ares | 2025 | 100+ | Onion Link |
| Cocorico | 2023 | 110+ | Onion Link |
| BlackSprut | 2023 | 300+ | Onion Link |
| Mega | 2016 | 400+ | Onion Link |
Updated 2025-07-12

Introduction to Online Privacy and the Tor Network
- The Tor Browser is a critical tool for accessing the dakrnet, providing a user-friendly interface that simplifies the process of maintaining anonymity.
- By leveraging the Tor Network, users can bypass censorship and access information that may be restricted in their region, further enhancing the utility of the dakrnet.
- The economic implications of the dakrnet are significant, as it provides a platform for free trade without the constraints of traditional regulatory frameworks.
The Tor Network has revolutionized the way individuals interact with the internet, offering unparalleled levels of anonymity and privacy. In an era where digital surveillance is pervasive, the need for secure communication channels has become paramount. The Tor Network, through its innovative use of onion routing, enables users to navigate the internet without revealing their identity or location. This technology has proven particularly valuable for those engaging in activities that require discretion, such as accessing the dakrnet, where goods and services are exchanged with minimal oversight.
The dakrnet, often misunderstood, serves as a marketplace for a wide range of products, including pharmaceuticals and other controlled substances. The decentralized nature of these platforms ensures that transactions remain confidential, fostering a sense of security among users. The Tor Network facilitates this by encrypting data multiple times and routing it through a series of nodes, making it nearly impossible to trace the origin or destination of the information. This level of protection is not only beneficial for privacy-conscious individuals but also for those who rely on the dakrnet for access to otherwise restricted goods.
While the Tor Network and the dakrnet are often associated with controversy, their role in promoting digital privacy and freedom cannot be overstated. By enabling secure and anonymous transactions, these technologies empower individuals to take control of their online presence, challenging the status quo of internet surveillance and control.
Understanding the Tor Network and Its Purpose
- The Tor Network enables users to bypass censorship and access information freely, particularly in regions with restrictive internet policies.
- It provides a secure environment for whistleblowers, journalists, and activists to communicate without fear of surveillance.
- The darknet marketplaces, accessible via Tor, offer a platform for the exchange of goods and services that are often unavailable through traditional channels.
The Tor Network is a decentralized system designed to enhance digital privacy and enable secure communication over the internet. By routing traffic through a series of volunteer-operated nodes, Tor obscures the origin and destination of data, making it difficult for third parties to track user activity. This architecture, known as onion routing, encrypts data in multiple layers, ensuring that each node only knows the immediate source and destination of the information it handles.
One of the most notable applications of the Tor Network is its role in facilitating access to the darknet, a subset of the internet not indexed by traditional search engines. The darknet hosts a variety of services, including marketplaces that operate outside conventional regulatory frameworks. These platforms often provide access to goods and services that are restricted or prohibited in certain jurisdictions, such as pharmaceuticals, digital tools, and other commodities. The decentralized nature of these marketplaces ensures a level of autonomy and privacy for both buyers and sellers, fostering a unique ecosystem of trade.
While the Tor Network is often associated with anonymity and privacy, it also plays a critical role in promoting economic freedom. By allowing individuals to engage in transactions without geographical or regulatory constraints, Tor contributes to a more open and inclusive digital economy. The network's ability to facilitate secure and private exchanges underscores its importance in the broader context of digital privacy and freedom of expression.
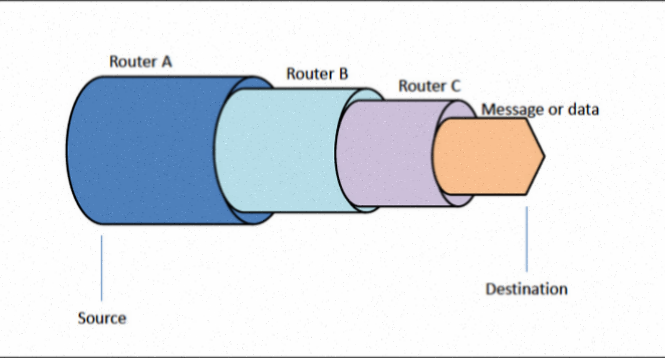
The Concept of Onion Routing and How It Works
- The entry node receives encrypted data and removes the outermost layer of encryption.
- The middle node further decrypts the data, ensuring no single point of failure.
- The exit node delivers the final decrypted data to its intended destination.
Onion routing is a sophisticated method of anonymous communication that forms the backbone of the Tor Network. It operates by encrypting data in multiple layers, akin to the layers of an onion, and routing it through a series of randomly selected nodes. Each node decrypts a single layer of encryption, revealing only the next destination in the chain, ensuring that no single node can trace the entire path of the data. This multi-layered encryption ensures that the origin and destination of the communication remain concealed, providing a high degree of anonymity.
The process begins when a user initiates a connection through the Tor Browser. The data is first encrypted by the client and then sent through a sequence of three nodes: the entry node, the middle node, and the exit node. Each node is operated by a different entity, making it nearly impossible for any single party to monitor the entire communication. The entry node knows the user's IP address but cannot see the content of the data, while the exit node can see the destination but cannot trace the data back to the user.
This architecture has made the Tor Network a vital tool for individuals seeking privacy in an increasingly surveilled digital landscape. It has also facilitated the growth of the dakrnet, where users can access a variety of services, including marketplaces for goods and services that prioritize privacy and security. The decentralized nature of these marketplaces ensures that transactions remain confidential, fostering a sense of trust among participants.
Despite its robust design, onion routing is not without challenges. The reliance on volunteer-operated nodes introduces potential vulnerabilities, such as the risk of malicious nodes attempting to compromise the network. However, the distributed nature of the Tor Network and its continuous evolution make it a resilient system for maintaining digital privacy.
The Tor Browser: A Tool for Anonymity and Secure Browsing
- The Tor Browser ensures end-to-end encryption, safeguarding user identities and transaction details.
- Marketplaces on the darknet often employ escrow systems, enhancing trust and reliability in transactions.
- The decentralized nature of these platforms reduces the risk of monopolization and promotes fair competition.
The Tor Browser serves as a gateway to the darknet, enabling users to explore a realm of digital privacy and anonymity. By leveraging the principles of onion routing, the browser encrypts data multiple times and routes it through a series of nodes, ensuring that user activity remains untraceable. This level of security is particularly valuable for individuals seeking to access darknet marketplaces, where a wide range of goods and services are exchanged with minimal oversight.
One of the most notable aspects of the darknet is its role in facilitating trade, including the exchange of substances that are often restricted in traditional markets. The Tor Browser provides a secure environment for such transactions, ensuring that both buyers and sellers can operate with reduced risk of exposure. This has led to the emergence of a robust and decentralized economy, where participants can engage in commerce without the constraints of conventional regulatory frameworks.
While the darknet is often associated with illicit activities, it is important to recognize its broader implications for digital privacy. The Tor Browser empowers users to reclaim control over their online presence, offering a level of anonymity that is increasingly rare in today's interconnected world. By providing a secure platform for communication and commerce, it challenges traditional notions of oversight and regulation, fostering a more open and equitable digital landscape.
Challenges and Vulnerabilities of the Tor Network
- The use of onion routing ensures that data packets are encrypted multiple times, making it nearly impossible to trace the origin or destination of communications.
- Cryptocurrencies like Bitcoin and Monero are frequently employed, offering an additional layer of anonymity for financial transactions.
- The decentralized structure of these marketplaces reduces the risk of single points of failure, ensuring continuity even in the face of external pressures.
The Tor Network has revolutionized the way individuals interact with the internet, offering unparalleled privacy and anonymity. However, it is not without its challenges and vulnerabilities. One of the most notable aspects of Tor is its role in facilitating access to the darknet, a space where users can engage in activities that prioritize privacy, including the exchange of goods and services. Among these, the trade of certain substances has become a significant part of the ecosystem, driven by the demand for secure and anonymous transactions.
The decentralized nature of the Tor Network ensures that users can operate without fear of surveillance, making it an attractive platform for those seeking to maintain confidentiality. This has led to the emergence of marketplaces that operate outside traditional regulatory frameworks, providing a unique environment for commerce. These platforms often utilize advanced encryption and cryptocurrency transactions, further enhancing security and reducing the risk of exposure.
Despite these advantages, the Tor Network is not immune to vulnerabilities. One of the primary concerns is the potential for exit node attacks, where malicious actors can intercept unencrypted traffic as it leaves the network. Additionally, the reliance on volunteer-operated nodes introduces the risk of compromised infrastructure, which could be exploited to de-anonymize users.
Another challenge lies in the evolving nature of cyber threats. As law enforcement and other entities develop more sophisticated methods of tracking and analysis, the need for continuous innovation within the Tor Network becomes paramount. This includes improving encryption protocols, enhancing node security, and fostering a community-driven approach to identifying and mitigating risks.
In conclusion, while the Tor Network provides a robust framework for privacy and anonymity, it is essential to recognize and address its vulnerabilities. By understanding these challenges, users can better navigate the complexities of the darknet and leverage its potential while minimizing risks.